Microsoft CA Certificate Provider
1. Prerequisites
In this section we describe the necessary configuration steps that must be performed in order for the Microsoft CA certificate provider to function properly.
1.1. Prepare SSH
Install an SSH server on one Windows server and optionally on a second server. Check whether OpenSSH is already installed (see Listing 1). Perform the operations in a PowerShell window which is run as administrator.
Get-WindowsCapability -Online | Where-Object Name -like 'OpenSSH*'The output is shown in Listing 2, in this example both the client and the server are not installed.
Name : OpenSSH.Client~~~~0.0.1.0
State : NotPresent
Name : OpenSSH.Server~~~~0.0.1.0
State : NotPresentInstall the SSH server, see Listing 3.
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0For more information see also Get started with OpenSSH for Windows.
1.2. SSH Server Availability
After restarting the computer where the SSH server runs, the service may be deactivated.
Either start the server over the services' configuration of Windows (open Services)
by starting the service OpenSSH SSH Server (see Figure 1), or
set the Startup type to Automatic (see Figure 1, under Properties).
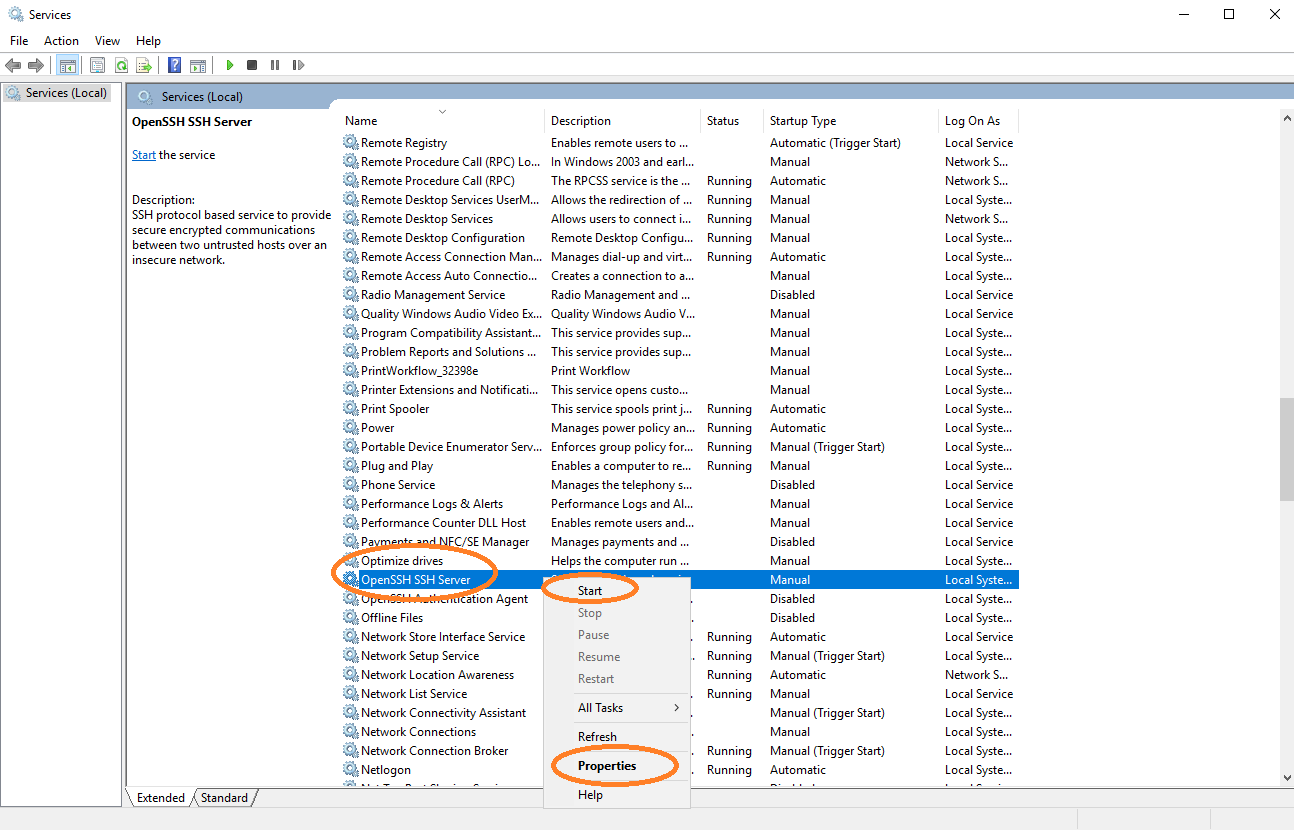
| Make sure the SSH server runs after a computer restart. |
You may repeat the steps described above in a second Windows server.
1.3. Template Management
Go to the server where Microsoft CA is installed.
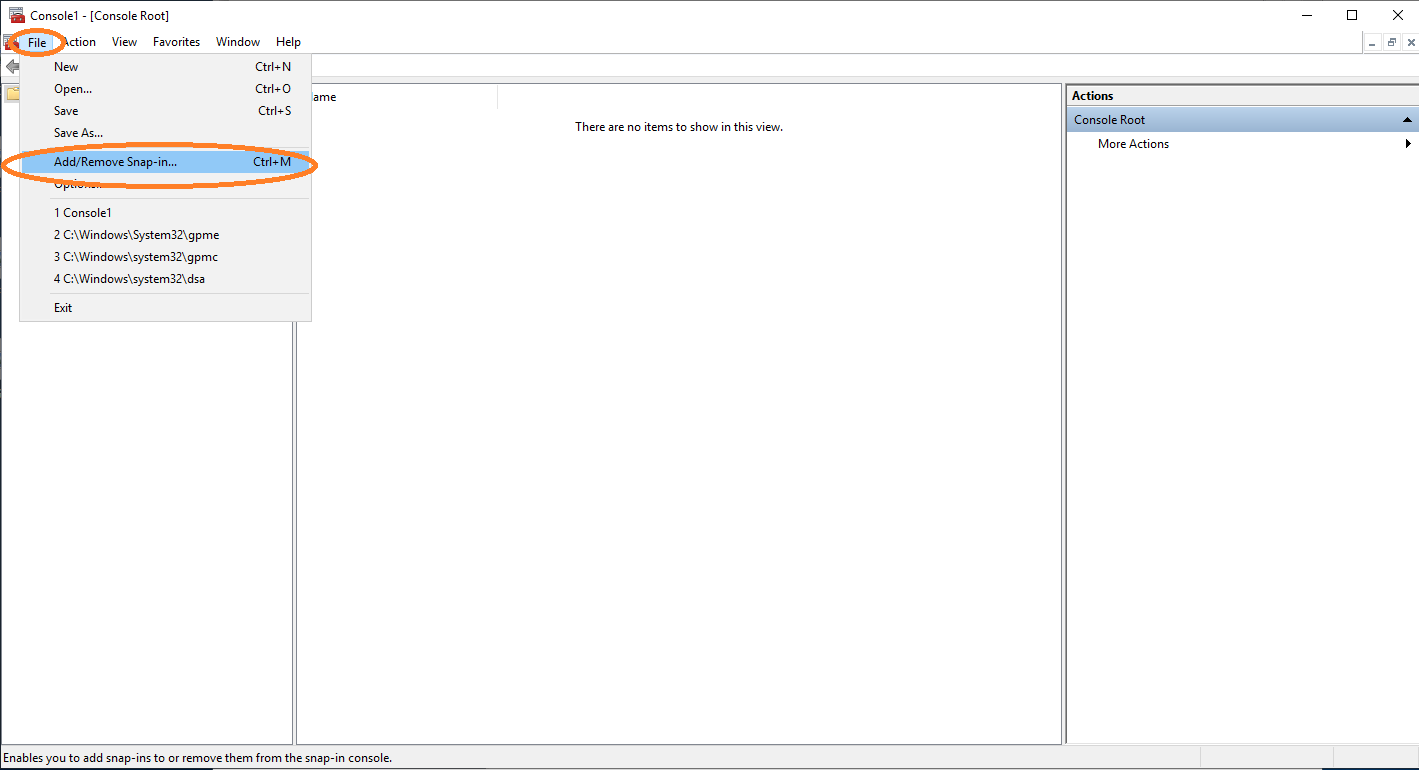
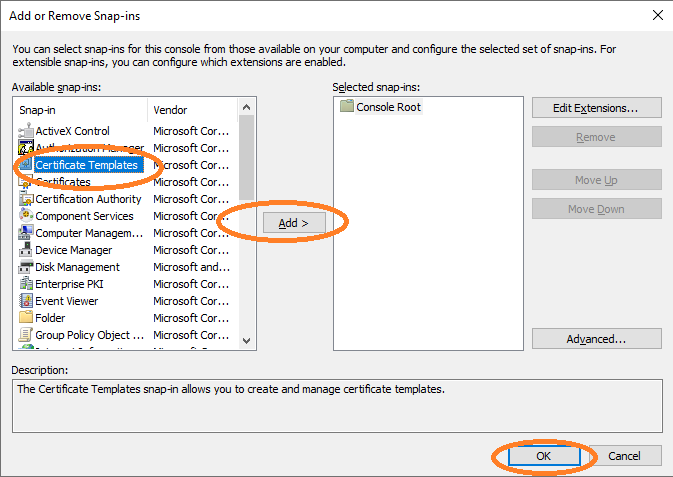
Open cmd and type mmc to get the Microsoft Management Console (see Figure 2) and add the certificate templates option, see Figure 3.
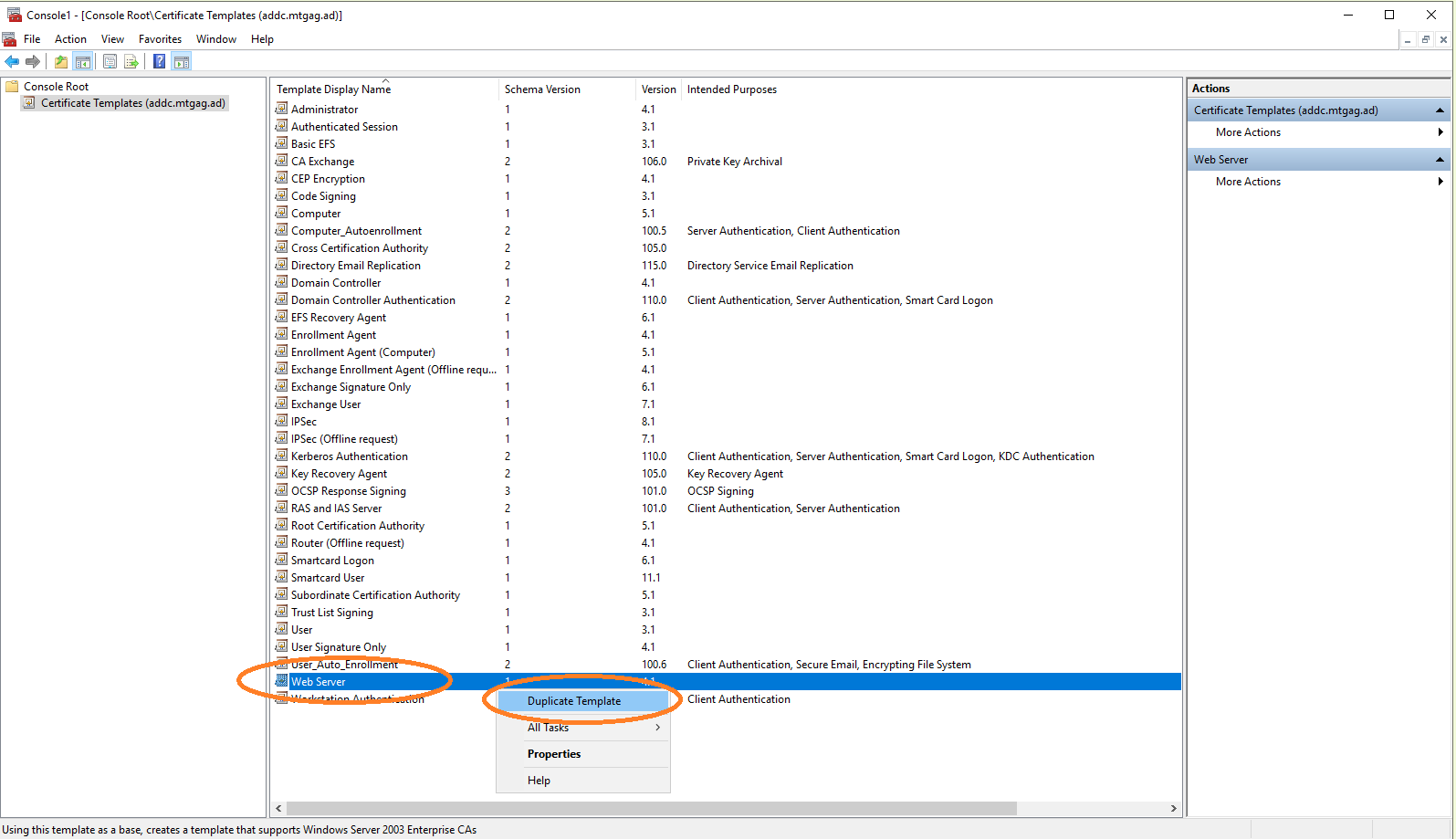
Then duplicate the Web Server template (see Figure 4) and
rename it to Web_Server_CLM. The name of the templates must always end with the suffix _CLM,
in order for templates to be located and be used by MTG Certificate Lifecycle Manager Server.
The templates that can be used by MTG Certificate Lifecycle Manager Server must always end with _CLM.
|
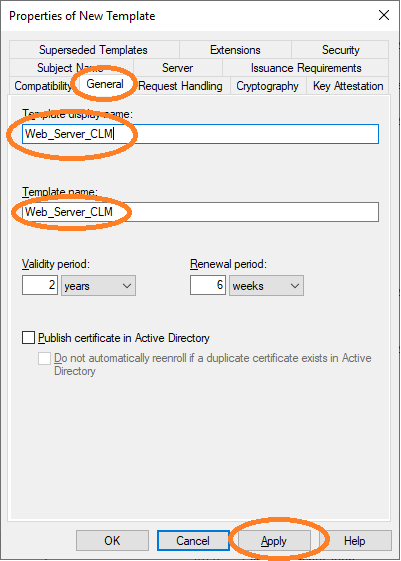
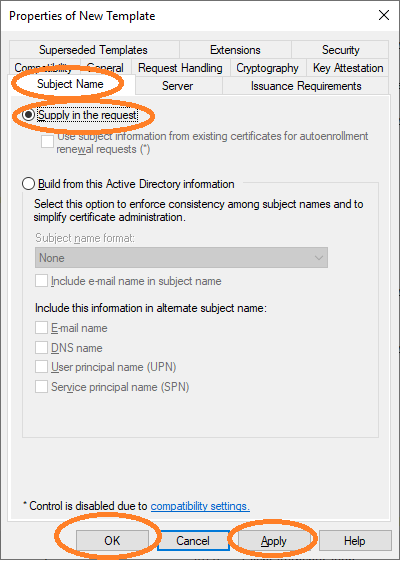
You may configure the new template Web_Server_CLM with the options of your choice.
Important is that the Subject Name must be configured to be supplied in the request
(see Figure 6).
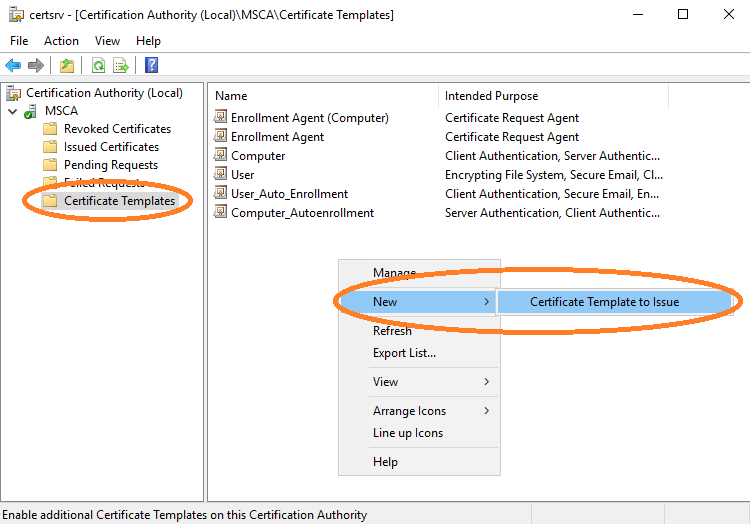
Lastly, you must configure the new template to the templates of
Microsoft CA. Open Certification Authority.
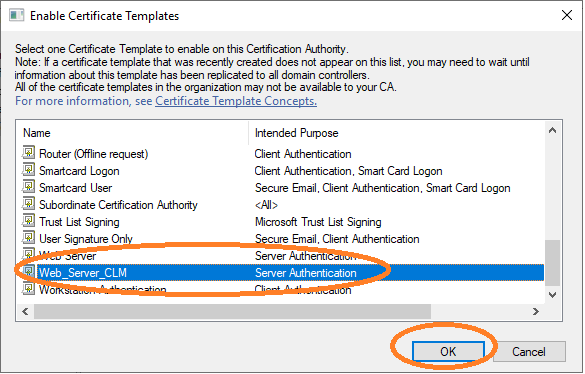
The Web_Server_CLM template now appears in the templates
that can be used by the Microsoft CA.
1.4. User Management
A new Windows user which is responsible for the requesting, approving,
and revoking certificates must be added and configured.
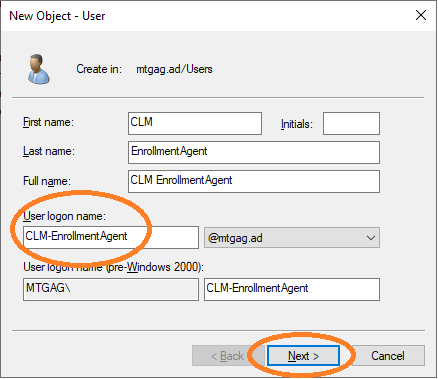
Choose the name CLM-EnrollmentAgent for this user,
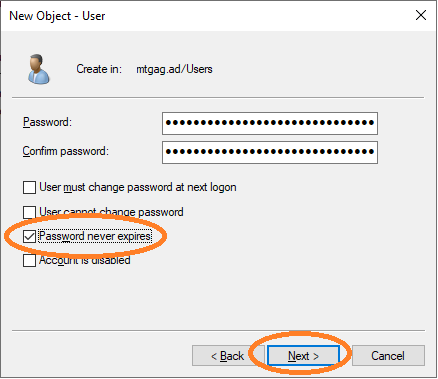
provide a password, and choose that this password never expires.
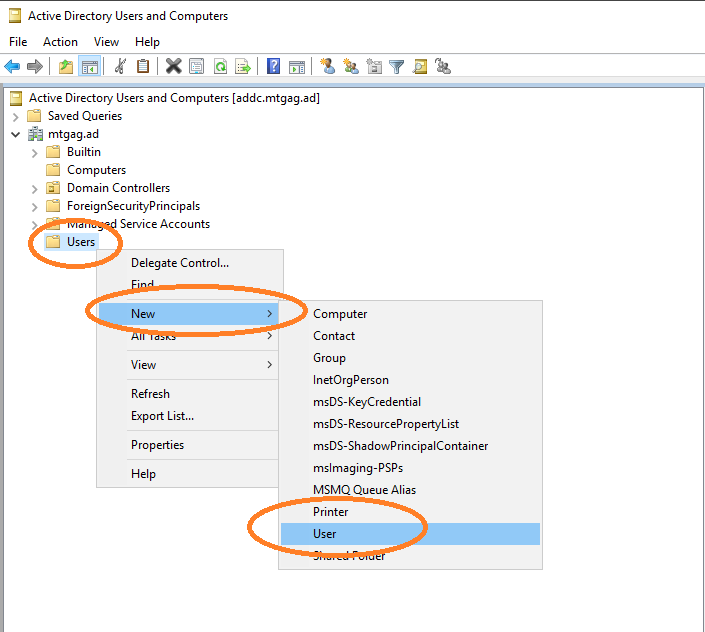
Open Active Directory Users and Computers. Then choose to add
new user, see Figure 9. Provide the User logon name, see Figure 10.
Lastly, provider the password and choose to never expire, see Figure 11.
1.5. Template Permissions
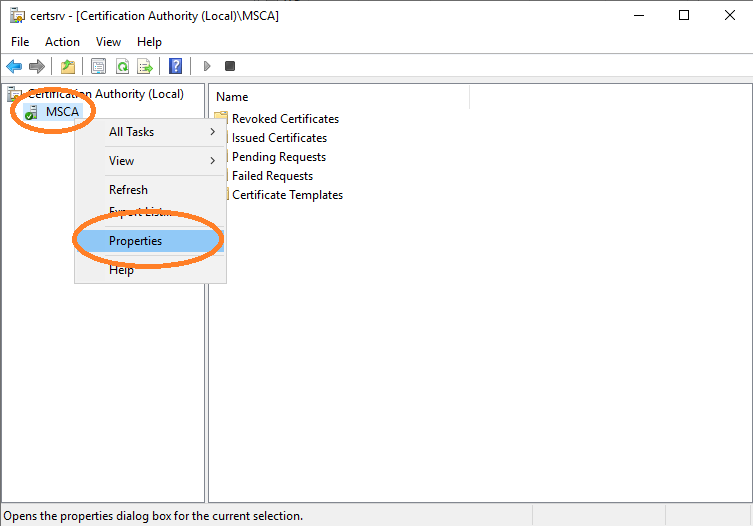
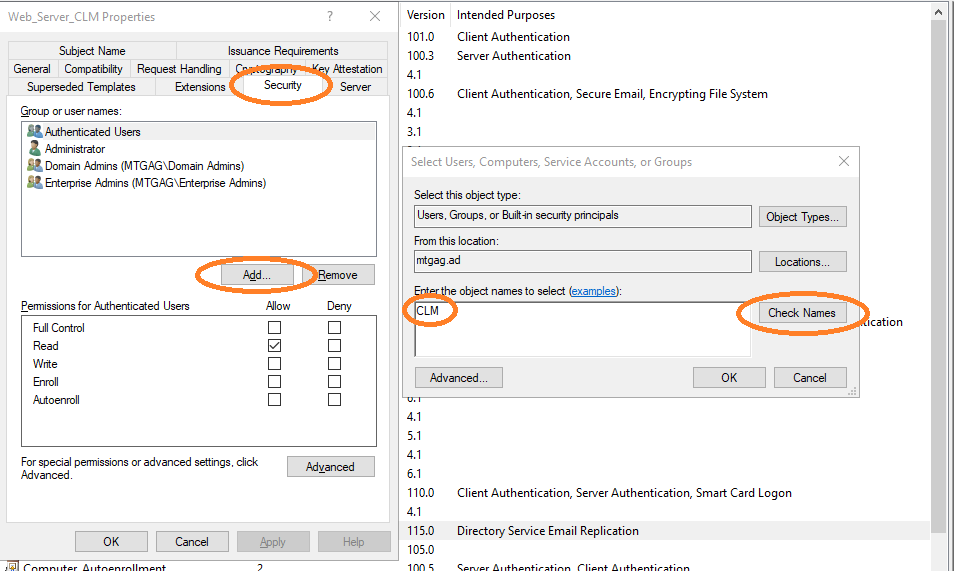
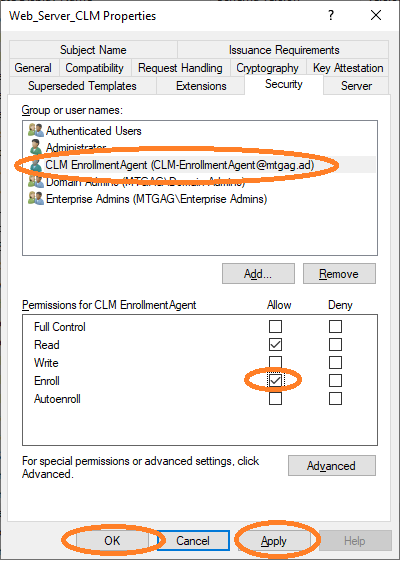
Finally, the CLM-EnrollmentAgent must be properly configured to be allowed to enroll certificates for this template. Navigate to the security properties of this template and add the CLM-EnrollmentUser (see Figure 12). Then allow the user to enroll certificates, see Figure 13. You should additionally disallow enroll access to this template for other users.
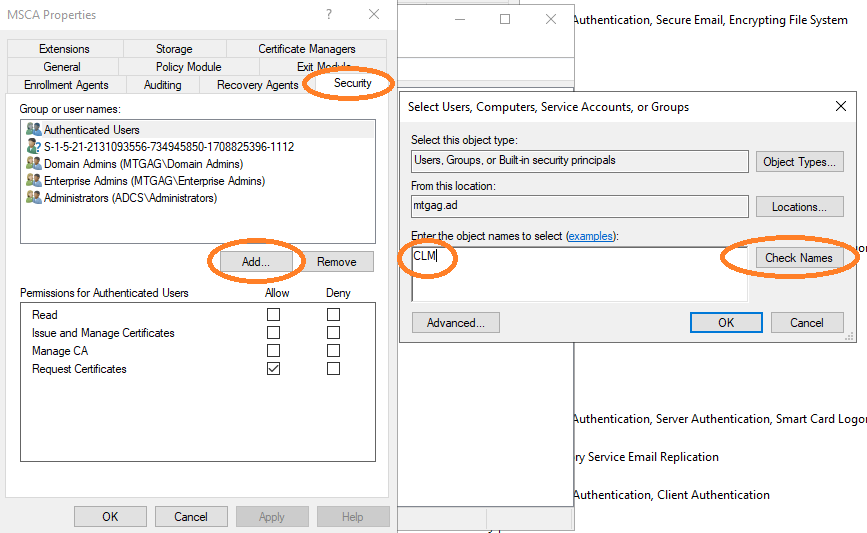
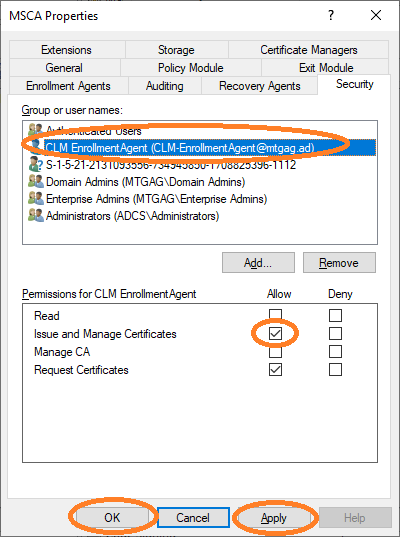
Additionally, this user must be configured to be able to revoke certificates. Navigate to the properties of the Microsoft CA (see Figure 14), then to the security properties to add the CLM-EnrollmentAgent user (see Figure 15), and finally allow this user to issue and manage certificates, see Figure 16. Now this user is able to issue and revoke certificates over the MTG Certificate Lifecycle Manager Server.